experts and translators of the new domain
Media
 Cybersecurity, An Introduction
Cybersecurity, An Introduction
By Paul Rosenzweig
This is our next great policy challenge.
Editor’s note: This essay is the first in a series of three articles by the author about cybersecurity and cyber warfare.
Hardly a day goes by without news of some new cyber attack or intrusion that causes widespread distress. On the day I started writing this article, for example, the hacker group Anonymous announced what it called “Military Meltdown Monday,” a large-scale hack of the IT system of Booz Allen, a major federal military contractor. The next day, there was a malware attack targeted at Frenchmen celebrating Bastille Day. Just a few days earlier, it had been Syrian security forces using social media to support President Bashar Assad against protesters. Still more frequently, it is a simple invasion of privacy, whether through the theft of identity, or the hacking of a voice mail system. And the list goes on. Vulnerability in cyberspace is our growing reality.
But why is cybersecurity such a challenge? And what does that vulnerability mean for our national security?
It is hard to understand cyber vulnerabilities, cybersecurity, and cyber warfare if you don’t understand how the web is built and why it works the way it does. To a very real degree, much of what we consider a vulnerability in the system is inherent in its design. Indeed, the internet is so effective precisely because it is designed to be an open system—and while that makes the network readily accessible, it also makes it highly vulnerable.
Vulnerability in cyberspace is our growing reality.

This is the famous “Peacock Map,” depicting the internet circa 2005. A map today would look very similar, but also completely different, since the connections on the network are ever-changing. What this map shows is that the internet is a vast switching system for the distribution of information at near instantaneous speeds across great distances. There are no borders on the internet and its structure makes action across global distances, without regard for national borders, the norm rather than the exception.
As Temple University professor David Post explained in his wonderful book, In Search of Jefferson’s Moose, the networks that make up cyberspace were built for ease of communication and expansion, not for security. At its core, the logic layer of the internet (more about that later) is fundamentally dumb. It is designed to do nothing more than transfer information quickly from one place to another—very quickly and very efficiently. So, even though most users tend to think of internet connections as nothing more than a glorified telephone network, the two are, in fact, fundamentally different.
The telephone networks are “hub and spoke” systems with the intelligent operation at the central switching points. Sophisticated switches route calls from one end to the other (indeed, at their inception, the intelligence at the hub of the telephone networks was human—operators making the required physical connections). By contrast, the internet is truly a “world wide web” of interconnected servers that do nothing more than switch packets of information around the globe. The intelligent operations occur at the edges (in our mobile devices and laptops running various “apps”).
This is the famous “Peacock Map,” depicting the internet circa 2005. A map today would look very similar, but also completely different, since the connections on the network are ever-changing. What this map shows is that the internet is a vast switching system for the distribution of information at near instantaneous speeds across great distances. There are no borders on the internet and its structure makes action across global distances, without regard for national borders, the norm rather than the exception.
And that’s what makes the internet so successful. Access to it is not controlled at a central switching point. You don’t need “permission” to add a new functionality. The way the internet is built, anyone with a new idea can design it and add it to the network by simply purchasing a domain name and renting server space. The addressing directory (known as the Domain Name System) that allows information to be correctly routed is operated on a distributed basis that no one person really controls. And, so long as the commonly accepted addressing protocols are used, virtually any function can be hooked up to the web—a store, a virtual world game site, or a government database. This flexibility is precisely what has driven the explosive growth of the internet. Today there are more than two billion users worldwide.
Let’s take a look at the structure that this wild growth has given us. When we talk colloquially of the internet, almost everyone is talking about the logical network layer where all of the information gets exchanged. If you tried to map all of these connections, this is roughly what it would look like:
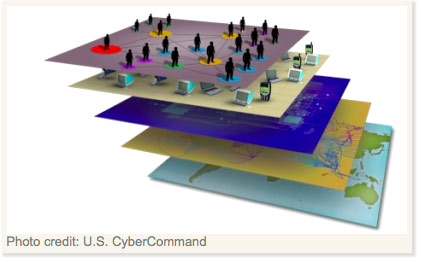 But this logic layer is only a piece of the puzzle. While most people think of the internet as the web of connections between computers, its full structure is really more complex. This graphic (created by and reprinted with the permission of US CyberCommand) gives you some idea of the scope of the entire cyber domain. It is, in essence, a five-layer cake of connections:
But this logic layer is only a piece of the puzzle. While most people think of the internet as the web of connections between computers, its full structure is really more complex. This graphic (created by and reprinted with the permission of US CyberCommand) gives you some idea of the scope of the entire cyber domain. It is, in essence, a five-layer cake of connections:
At the bottom is what we might call the Geographic layer—that is, the physical location of elements of the network. Though cyberspace itself has no physical existence, every piece of equipment that creates it is physically located somewhere in the world.
Next is the Physical Network layer. This is the place where all of the hardware and infrastructure exists and is connected together. The components of this layer include all of the wires, fiber optic cables, routers, servers, and computers linked together across geographic spaces (some of the links are through wireless connections with physical endpoints). Above this is the middle layer, the heart of the internet—this is the Logic Network layer we’ve already seen. This is the virtual space where the information resides and is transmitted and routed by servers. Here packets of information—the 1’s and 0’s of binary code—are distributed by a switching system that operates autonomously, without human direction.
But what does that vulnerability mean for our national security?
The logic layer in turn needs to be connected to the users. So, above the network layer is the Cyber Persona layer. In this layer we see how a user is identified on the network—this could be by his email address, computer IP address, or cell phone number. Most individuals have many different cyber persona—just think of how many different email addresses and phone numbers you have.
Finally, there is the Persona layer. This is where the actual people who are using the network and have their fingers on the keyboards, so to speak, exist. While an individual can have multiple cyber personas (and, conversely, a single cyber persona can have multiple users), in the end, we can also think about uniquely identifying a particular person connected to the network.
***
Deputy Secretary of Defense William Lynn summed up this structure in a speech announcing our military Strategy for Operating in Cyberspace: “The internet was designed to be open, transparent, and interoperable. Security and identity management were secondary objectives in system design. This lower emphasis on security in the internet’s initial design . . . gives attackers a built-in advantage.” And it gives rise to significant vulnerabilities in at least three ways.
The first vulnerability is the problem of anonymity. Given the vastness of the web, it is quite possible for those who seek to do harm to do so at a distance, cloaked in the veil of anonymity behind a false or ever changing cyber persona. While we can overcome this vulnerability, doing so requires a very great investment of time and resources. It also often requires the “good guys” to use “bad guy” techniques to track the malefactors. In effect, this makes many malfeasant actors immune, for all practical purposes, from swift and sure response or retaliation.
The second vulnerability lies in the difficulty of distinction. All the 1s and 0s in the logic layer look the same. But that means that different types of activities in the logic layer are hard to distinguish. Put another way, any successful cyber attack or intrusion requires “a vulnerability, access to that vulnerability, and a payload to be executed.” But in practice, the first two parts of that equation (identifying a vulnerability and gaining access to it in the logic layer) are the same no matter what the payload that is to be delivered.
The ubiquity of the internet creates asymmetries of power.
Thus, for those on the defensive end, it is virtually impossible to distinguish ex ante between espionage, and a full-scale cyber attack. They all look the same at the front end—and all three also often look like authorized communications. The difference arises only when the payload is executed and the effects are felt. The closest real world analogy would be never being able to tell whether the plane flying across your border was a friendly commercial aircraft, a spy plane, or a bomber.
Finally, the ubiquity of the internet creates asymmetries of power. Where, in the kinetic world, only nation states could effectively compete against each other, in the cyber domain, small non-state actors can challenge nation states, and poor Nigerian con artists can scam people on a global scale. One individual with multiple, complex relationships to other levels of the environment can send anything through the network to virtually any location worldwide. And with that, we empower small groups like Anonymous (the cyber hacktivists who attacked PayPal, Amazon, and MasterCard) to, in effect, make all sorts of mischief.
The very structures that make the internet such a powerful engine for social activity and that have allowed its explosive, world-altering growth are also the factors that give rise to the vulnerabilities in the network. We could eliminate anonymity and resolve distinction, but only at the price of changing the ease with which one can use the internet for novel commercial and social functions. Those who want both ubiquity and security are asking to have their cake and eat it to. So long as this internet is The Internet, vulnerability is here to stay. It can be managed but it can’t be eliminated.
Paul Rosenzweig, Esq., is the founder of Red Branch Law & Consulting, PLLC. Rosenzweig formerly served as deputy assistant secretary for policy in the Department of Homeland Security and twice as acting assistant secretary for international affairs. Rosenzweig is a professorial lecturer in Law at George Washington University and a visiting fellow at the Heritage Foundation. He serves as a senior editor of the Journal of National Security Law & Policy.
Rosenzweig is a cum laude graduate of the University of Chicago Law School. He is the coauthor (with James Jay Carafano) of the book Winning the Long War: Lessons from the Cold War for Defeating Terrorism and Preserving Freedom and author of the book Cyberwarfare: How Conflicts in Cyberspace Are Challenging America and Changing the World.
The essay above is based on a book by the author titled, Cyberwarfare: How Conflicts in Cyberspace are Challenging America and Changing the World.
Letters to the editor may be sent to definingideas@stanford.edu. Editors reserve the right to reject or publish (and edit) letters.
