experts and translators of the new domain
Media
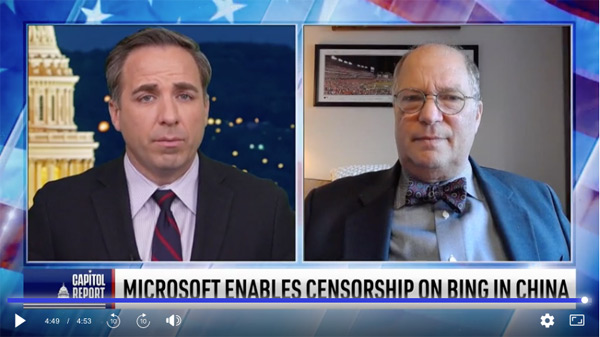 Microsoft is at the Heart of US National Security Systems and It’s Vulnerable: Cyber Security Expert
Microsoft is at the Heart of US National Security Systems and It’s Vulnerable: Cyber Security Expert
Rep. Brendan Boyle recently (D-Pa.) wrote a letter to Microsoft about how close they are to the Chinese Communist regime. Joining us now to assess the risks of Microsoft’s ties to the CCP, we have cyber security expert Paul Rosenzweig.
 Jack Smith’s Daring Gambit
Jack Smith’s Daring Gambit
Donald Trump’s frivolous claim of absolute immunity looks to be heading to the Supreme Court, with massive consequences both for him and for the future of American democracy.
By Paul Rosenzweig
Donald Trump’s trial on charges that he tried to overthrow the election will almost certainly not happen in March 2024, as many had hoped. If it doesn’t, Trump will have once again demonstrated that a commitment to due process is the Achilles’ heel of democracy. While democracy’s defenders play by the rules and the rule of law, Trump bends the law to his own purposes.
That is the only conclusion one can reasonably draw from the latest Special Counsel filing, which asks the Supreme Court to hear immediately Trump’s claim of absolute immunity from prosecution. The claim is nonsensical, and the Special Counsel’s request for Supreme Court review is understandable (indeed, even commendable), but once again, Trump has succeeded in weaponizing the judicial process to his own advantage, using the delay that comes with Supreme Court review to postpone his trial to a more politically advantageous time for him…
National Security
Obama orders voluntary security standards for critical industries’ computer networks
By Ellen Nakashima, Washington Post
Citing the growing threat from cyberattacks, President Obama on Tuesday announced that he had signed an executive order that calls for the creation of voluntary standards to boost the security of computer networks in critical industries such as those that keep trains from colliding and drinking water clean.
“We know hackers steal people’s identities and infiltrate private e-mail,” he said in his State of the Union speech. “We know foreign countries and companies swipe our corporate secrets. Now our enemies are also seeking the ability to sabotage our power grid, our financial institutions, and our air traffic control systems. We cannot look back years from now and wonder why we did nothing in the face of real threats to our security and our economy.”
Read full text…
 National Security Law in the News
National Security Law in the News
Much in America changed on September 11, 2001.
One of those changes was the language of discourse in our public dialog about war and terrorism. But few realize that a robust and detailed body of law and policy lies behind that dialog. This new guide will demystify that law and policy by providing the necessary legal background and context for journalists and others who want to understand ongoing policy debates.
Written by seasoned experts, each chapter contains a summary of legal and policy issues of significance and is accompanied by an annotated bibliography for further reading. The book is divided into four parts:
Read full text…
 Cybersecurity, An Introduction
Cybersecurity, An Introduction
By Paul Rosenzweig
This is our next great policy challenge.
Editor’s note: This essay is the first in a series of three articles by the author about cybersecurity and cyber warfare.
Hardly a day goes by without news of some new cyber attack or intrusion that causes widespread distress. On the day I started writing this article, for example, the hacker group Anonymous announced what it called “Military Meltdown Monday,” a large-scale hack of the IT system of Booz Allen, a major federal military contractor. The next day, there was a malware attack targeted at Frenchmen celebrating Bastille Day. Just a few days earlier, it had been Syrian security forces using social media to support President Bashar Assad against protesters. Still more frequently, it is a simple invasion of privacy, whether through the theft of identity, or the hacking of a voice mail system. And the list goes on. Vulnerability in cyberspace is our growing reality.
But why is cybersecurity such a challenge? And what does that vulnerability mean for our national security?
Read full text…
 From Worms to Cyber War
From Worms to Cyber War
By Paul Rosenzweig
In just a generation, viruses went from being a novelty to a worldwide threat.
Editor’s note: This article is the second in a series of three articles about cybersecurity and cyberwarfare that will be published periodically in Defining Ideas. The first article, Cybersecurity: An Introduction, can be found at the following link.
The first known virus ever to infect a personal computer was named “Brain.A.” It was developed (dare we say invented?) by two Pakistani brothers Basit and Amjad Alvi. We know this because, amusingly, they signed their work and included contact information in the code of the virus. Brain. A was first detected in January 1986, just over 25 years ago. In its initial form, the virus did no significant harm. It renamed a volume label (in effect a file name) to “Brain” and could freeze a computer. Basit and Amjad say they meant no harm from their creation. How the world has changed! In just a single generation, we have gone from viruses being a novelty, to them being very real threats to cyberspace.
Read full text…
 Beware of Cyber China
Beware of Cyber China
By Paul Rosenzweig
How should we define an “act of war” in the virtual world of the internet?
Editor’s note: This is the third in a series of articles about cybersecurity and cyber warfare that will be published periodically in Defining Ideas. Earlier articles in the series are available here.
Cyberspace is awash in vulnerabilities. Actors in the cyber domain are wise to protect against crime, espionage, and hacktivist intrusions. But while those vulnerabilities are all too real, they are not driving the policy debate today in Washington. Instead, what seems to have seized the imagination of so many is the prospect of a true cyberwar.
But we’ve never had a real cyberwar (though the Russian attack on Georgia comes close), so there is no solid data on the threats that exist. We can only assess the potential for cyberwar by measuring the capabilities or our possible adversaries, and then only by educated guess work. We have no clear sense of true intent. As a result we lack a solid quantifiable risk assessment of the cyber threat to national security and this leaves policy makers only with speculation as to the extent of our risk from a cyber attack by a willful cyber opponent.
The uncertainty does not, however, prevent us from thinking about the problem. We struggle today with two inter-related questions: Who are we likely to fight? And how are we going to fight them?
Read full text…
 National Security Experts Discuss Need for Cybersecurity Cooperation
National Security Experts Discuss Need for Cybersecurity Cooperation
Around the Bar
The nation’s defense secrets are stolen by hackers working out of an Internet café in Seoul, South Korea and auctioned to the highest bidder. Millions lose power for more than a week during a heat wave due to an invasive computer program that targets electric utilities. The names, birthdates and Social Security numbers of company employees are stolen by organized crime.
National security experts gathered Aug. 3 at the American Bar Association Annual Meeting in Chicago to discuss the growing risk posed by hackers and foreign powers that could infiltrate and disrupt the technology that keeps the United States running.
Suzanne Spaulding, the deputy under secretary for the National Protection and Programs Directorate at the Department of Homeland Security, urged those speaking about cybersecurity matters to “disaggregate the threat.”
Read full text…
 Paul Rosenzweig on Harold Koh’s Duty of Loyalty
Paul Rosenzweig on Harold Koh’s Duty of Loyalty
By Kenneth Anderson
Following the splendid University of Virginia School of Law conference last Friday at which DOS Legal Adviser Harold Koh delivered the keynote address, Notre Dame professor and Opinio Juris blogger Roger Alford commented on part of Koh’s speech in which he defended himself against various charges of inconsistency and even hypocrisy in not holding to all the views he expressed as an academic over several decades. Alford defended him against this charge in agreeing that his role involves an important one as a lawyer with a client; Legal Adviser Koh is not Dean Koh, intellectual-free-agent professor.
Over at Volokh Conspiracy, I agreed with Alford and added that this applied still further, in that his role involved more than just attorney-client duties, but the general fiduciary duty of a public official in a position of public trust, something true of public officials generally and not just the lawyers. Paul Rosenzweig dropped me an email, which he kindly allows me to post here, agreeing with the first two, and adding a third layer – that public officials in an administration moreover have a duty of loyalty to the president. All three of us, then – Alford, Rosenzweig, and I – broadly agree that academics and others who accuse Koh of hypocrisy for somehow not following views he expressed as an academic are mistaken and not in small ways. As Rosenzweig says (speaking informally in a personal email):
Read full text…
Taming the Cyber Dragon?
By Paul Rosenzweig
While Ben has often mocked the New York Times for its opinions, the Washington Post has mostly escaped our attention. To a large degree this reflects the level-headedness of its opinions. So when it slips into an alternate universe of unreality, that likely reflects something important. Consider yesterday’s editorial opinion calling for the US to do more to “tame the cyber dragon.”
The Post rightly notes that China is stealing us blind — intellectual property and national security secrets are being exfiltrated through cyberspace on an industrial scale. And though China denies any responsibility, its denials are the barest fig leaf of an effort. As the Post says, there is growing evidence that China is behind one of the largest heists in history. And something must be done.




 National Security Law in the News
National Security Law in the News Cybersecurity, An Introduction
Cybersecurity, An Introduction National Security Experts Discuss Need for Cybersecurity Cooperation
National Security Experts Discuss Need for Cybersecurity Cooperation Paul Rosenzweig on Harold Koh’s Duty of Loyalty
Paul Rosenzweig on Harold Koh’s Duty of Loyalty